Posted on Wednesday, 1st July 2015 by Michael
Google Android Device Manager to the Rescue
Let’s start off by me explaining how I found out how great the Android Device Manager is. My wonderful wife came home from a trip to the local farmers market the other day all upset about losing her new Samsung galaxy S6 while running through a nasty rain storm with our newborn son. This is the same device she stores all the pictures she takes of our newborn son. When she realized it was missing she was super distraught.
When she told me about what happened I explained the likely hood of getting the device or the data back would be very slim especially since we did not have any software on the phone to track the device or recover data. At that point I started to formulate a plan of attack to stop any further loss of data such as changing passwords on all accounts associated with the phone, freezing service and checking her backup cloud account to see what data we can recover.
That’s when I took my own advice I always tell her to do, Stop, Think, Act! I decided to give the situation a quick google in the event I could find a way to locate the phone or do a remote wipe. I found many articles on how to use third party tools that had already been installed on your device to locate the device, recover data and or wipe the device. Though deep down in my searching I found a link on how to use the ADM to track and secure a lost phone.
ADM can be installed on your android from the Google play store. Installing the ADM on your phone allows you to search for other people’s devices by using guest mode. You can also use the web ui on a PC or MAC: https://www.google.com/android/devicemanager . The only piece of information you will need is the user’s Google account (GMAIL).
Once you log into the ADM you can select the device you want to Track, Secure or Wipe from the list if you have multiple devices connected.
Below you can see an example from the web UI:
Tracking:
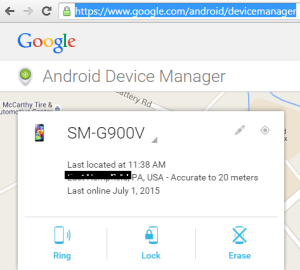
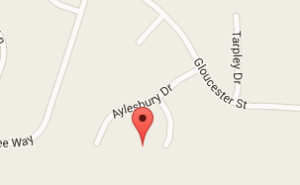
I have redacted my location for privacy. Below you can see the current location of my phone on the map, Google states it is accurate within 20 meters:
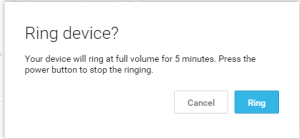
Below you can see what happens when you choose Ring. This feature is great if your phone is on vibrate or silent. It will enable your ringer at the highest volume for 5 minutes of continuous ringing.
Securing:
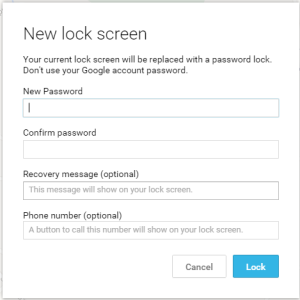
Below you can see the features of using the lock option. This is great if you do not have a pin on your device and you want to make sure no one can access the data on the device while you try to recover it.
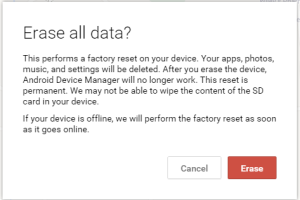
Wiping:
Below you can see the options of using the wipe option. Note this will remove all data though a great option if the phone is stolen and to make sure no data can be accessed on it. However per the feature it may not wipe the contents of your SD which can be pulled from the phone and accessed on a PC if not encrypted.
After exploring the options inside of the ADM. I am happy to report that the once upset wife was made happy when I told her phone was somewhere on our property and even more delighted when I made it start ringing (she had it on silent), which led to its finding wedged between the seats of her mother’s car.
Moral of the story always STOP, THINK, ACT.
- Make backups of your devices often.
- Have a Pin on your device
- Be prepared to wipe the device if need be.
- Change all passwords for applications that are not needed in a recovery attempt.
Posted in Uncategorized | Comments (0)




