Posted on Saturday, 26th September 2009 by Michael
A little command line FU for you. Small but effective Free IPS and Firewall.
First off here are a few caveats that I need to mention before I get bombarded by people complaining that it does not always work.
- This requires a state full connection IE. icmp will not get detected.
- The connection may get missed if it is only 1 packet IE. Netsend.
- Since this uses a loop there may be a delay and you may miss the connection.
This all started when last Friday my computer popped up a message saying it was about to reboot and one of my new co workers started laughing at my displeasure so I knew he did something. Turns out he was just learning how to use Pstools to execute commands and other things. If you do not know what Pstools are I suggest you Google it as they are some powerful free tools written by a security researcher and purchased by Microsoft. For those that know what Pstools are and are asking yourself why he has admin to my machine in the first place, the answer is simple we are members of the security team we have admin over all machines in the domain (not domain admin) so we can do our job duties when asked. We will leave it at that, knowing that if I was allowed to and able to I would remove everyone from my machine that did not need access to it.
Normally I would have just laughed along with him but I was working on a report and this basically made me pull out all stops. To buy me some time and offer a quick retribution I created a bat file with the following code in it and placed it in his user profile start up.
@echo off
psshutdown.exe -m “HAHA”
Note I did not have to supply the path to the psshutdown command as my co worker was nice enough to make my job easier and put Pstools into his environment for me.
The command above will basically display the message HAHA as it countdowns 20 seconds before shutting down his machine. By placing it in his user profile startup it would shutdown the machine every time he logged in. I did it this way so any one of the team could still log in and fix the machine in case he could not figure this out.
Once this was done I executed the command psshutdown.exe \\HIS_IP –m “HAHA” manually to start the fun. Once he realized that every time he was to log in his machine was to reboot. I informed him if you want to hack you need to learn how to protect against hacks and how to investigate compromised machines. I told him to think about what is happening and what could be causing it to happen. After a few tries he finally figured it out and corrected the issues.
This leads me into why I am writing this article and the code that you are probably here to see. After him rebooting me and knowing that it could happen again at any given time I started pondering different ways I could detect and counter future attempts without having to purchase any software or installing any tools from internet. I knew in Linux I could use the netstat command and grep to find his IP when a connection is made to me and then pipe that IP into another command such as adding it to the host.deny list or to a firewall rule or even going as far as using metaploit to attack him back automatically. But unfortunately we do not run Linux desktop environments so I was stuck with a windows environment and basic knowledge of windows scripting. I find it annoying that I could write a Linux shell script that could take over the world (not really but you get the point) in my sleep but it takes me a few days of research and trial and errors to write a windows batch file. I think most of it has to deal with the fact I just never really needed to do them as often as I have had to do them on Linux and when I have I usually just used Perl or CGYWIN but I degress. So based on what I know I could do on Linux I started to think about what I could do on windows to offer a layer of protection and I came up with this with help from another co-worker:
@echo off
:top
for %%a in (192.168.1.2 192.168.1.3 192.168.1.4) do call :SubRoutine %%a
goto top
:SubRoutine
netstat -an | find “%1”
if “%errorlevel%” NEQ “0” goto end
echo “ATTACKER DETECTED”
psshutdown.exe -m “HAHAHA your bad” \\%1
goto end
:end
This script will basically continue to run monitoring the netstat command output every second to look for the IP addresses I have supplied to it. If the IP is found it will give error code 0 meaning it was successful and then execute the psshutdown command against that box stopping the attack and shutting down the attacker.
Now I know what you are thinking, this only works if you have admin on their box and you are correct. This also does not assume they are not attacking you and are actually connecting to you for a business need. So let’s first address the issue of you not being admin and what options you are then left with to protect yourself. Unfortunately the windows firewall is not very useful it takes all or nothing approach and does not allow individual IP or port blocking. It basically says if on and no exception then block everything. So to administrate something like that from a batch file on the fly is not very sufficient. Actually windows itself truelly lacks the ability to easily and quickly respond. There is no host.deny or Iptables or service.deny like in Linux. You could possibly learn how to use PKI and IPSEC ; and right rules to do that stuff in there based on systems though that is extremely tough for most windows users.
This led me to search on the internet for a way to close connections via the windows command line. Several of the tools I found such as TCPKill or WinTCPKill were automatically deleted by McAfee because they are considered hacking tools. So I continued to look for a tool that would work and was safe for use, not saying those other tools are not safe though McAfee is a requirement here. The tool I found was CurrPorts by the guys over at http://www.nirsoft.net/utils/cports.html . Using this tool let’s take a look at what the code will now look like:
@echo off
:top
for %%a in (192.168.1.2 192.168.1.3 192.168.1.4) do call :SubRoutine %%a
goto top
:SubRoutine
netstat -an | find “%1”
if “%errorlevel%” NEQ “0” goto end
echo “ATTACKER DETECTED”
cports.exe /close * * %1 *
goto end
:end
As you can see above we replaced the “psshutdown” command with the “cports.exe” command. The syntax above uses the /close flag which closes established connections. The * * refers to the local host and the source port. The asterisk allows for wildcards. The %1 is the IP address we want to close and the last * is for the remote port. This seems to work 99% of the time. In our testing we noticed that if a person tried to connect to a port this killed the connection. If they did something like an http request there was a chance we missed the connection since it is not on going. We also noticed that it did not catch share access. We did notice it stopped logins, net cat, telnet, ftp, pstools and more.
Here is a screenshot of the attack without getting blocked by my script:
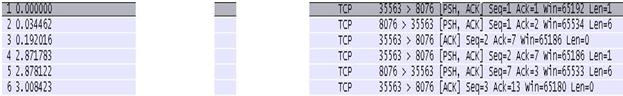
Here is a screenshot of the attack being blocked by my script. As you can see I am sending a “RST” flag to the attacker to reset their connection which basically kills the handshake and connection:

Now that we addressed not having administrator access and still being able to help block unwanted attacks let’s look at extending this script to be able to capture the port as well. This will be useful as you will see shortly.
@echo off
:top
for %%a in (192.168.1.2 192.168.1.3 192.168.1.4) do call :SubRoutine %%a
goto top
:SubRoutine
for /f “tokens=2” %%a in (‘netstat -an^|find “%1″‘) do set IPnPort=%%a
for /f “tokens=1-2 delims=:” %%b in (‘echo %IPnPort%’) do (
set IP=%%b
set Port=%%c
)
set IPnPort=
if “%IP%”==”” goto end
if “%Port%”==”” goto end
echo ATTACKER DETECTED from %IP% on Port %Port%
cports /close * * %1 %Port%
for %%a in (IP Port) do set %%a=
goto end
:end
The code above allows us to search for the IP address and when the IP is detected it will save the value IP:PORT into the temp variable %IPnPort% it will then run that variable through one more for loop to get the IP and port as two separate variables in this case %%b and %%c which is then turned in the variables %IP% and %Port%. Once we have these two variables we can do a multitude of things. In the sample above we used the variables to specify the IP and port to have cports.exe close. Even though we could of just used an *. In theory we could add another for loop that contained a list of allowed ports and if %Port% was equal to an allowed port it would not kill the connection.
We can also use another third party tool called plink which is part of the putty suite of tools. Plink is a self contained executable that allows you to use the same protocols you find in Putty but via the command line. It also has a very useful flag that allows for a lot of power. The “-m” flag will allow you to send a configuration to a box. For an example we could have our script above use the echo command to write firewall rules to a txt file. We can then use Plink to connect to the firewall and write the rules to the firewall providing an instant protection scheme. This is extremely helpful for those that run Juniper Netscreen (SSG or earlier) firewalls or CISCO Pix / ASA firewalls. I am not going to cover the syntax for adding rules to the firewalls via the command line for those two firewalls in this paper but I will give you an example. Let’s take the above code and remove the “cports /close” line and add this line instead.
echo “ set %IP% any eq %Port% deny log” >> fw-rules.txt
echo “set any %IP% eq %Port% deny log” >> fw-rules.txt
echo “wr mem” >> fw-rules.txt
plink USERNAME@HOSTNAME -pw PASSWORD -m fw-rules.txt
>> fw-rules.txt
This code will basically create the firewall rules to deny all connections inbound and outbound to the IP address and port you specified via the variables. Once again the syntax of the rules is not correct but it gives you the insight on what can be done. All you have to do is echo into the fw-rules.txt file any commands you need for your firewall.
To expand this script you can use one other third party tool called “wget” there is a windows port that can be found at http://gnuwin32.sourceforge.net/packages/wget.htm. With this tool you can download lists of blocked IP addresses from different sites on the internet and incorporate it into your script. So if the script detects one of these malicious IP’s are trying to connect to you can auto block it and log it. To do this we can alter the code like this:
@echo off
wget http://somesite.com/ip.txt
:top
for /f %%a in (ip.txt) do call :SubRoutine %%a
goto top
:SubRoutine
for /f “tokens=2” %%a in (‘netstat -an^|find “%1″‘) do set IPnPort=%%a
for /f “tokens=1-2 delims=:” %%b in (‘echo %IPnPort%’) do (
set IP=%%b
set Port=%%c
)
set IPnPort=
if “%IP%”==”” goto end
if “%Port%”==”” goto end
echo ATTACKER DETECTED from %IP% on Port %Port%
ATTACK CODE GOES HERE
for %%a in (IP Port) do set %%a=
goto end
:end
The code above will download a list of known malicious bad sites and monitor connection attempts from those IP addresses against your computer. It will respond to the connection attempt based on the response you want to use. I have give n you several possible responses throughout this paper though don’t limit yourself to those. Use your imagination to expand on this code to make it work for you.
I want to thank you all for reading this and if you have any questions or comments please feel free to contact me. I also want to give special thanks to RunCmd aka Neil for his killer windows scripting skills and patience in helping me.
Posted in Papers | Comments (1)